
Computer viruses and other malicious programs, generally called “malware” are a significant problem online. If you become infected, it can cause problems for your computer, for your local network, for your ISP, and really for a lot of other people. You want to keep your computer as clean as you can. I’ll talk about some ways to avoid malware online.
There are two very basic methods to avoid malware, and you should use them both to stay safe:
- Run decent anti-virus packages.
- Have good online hygiene.
Even if you are perfect with both of these, you will occasionally get something. If you do it right though, it will be fairly seldom. I’m very careful. I have only ever encountered two or three viruses on my own hardware since I first went online in the mid-’90s. I run regular virus scans which come up blank, and I run active virus scanning, which pops up with a threat detected about once a decade. As I said I’m fairly careful, and my infections, which were fairly easy to clean, happened because I got careless. For the most part, I successfully avoid malware online.
I personally have only been fooled a time or two, on the other hand, I also helped one person where a virus scan showed over 5000 threats. After cleaning those off, a second scan showed several thousand more. I ended up having to wipe everything and reinstall on that one. Cleaning a few viruses, is one thing, cleaning tens of thousands is something else entirely.
Why does malware exist?
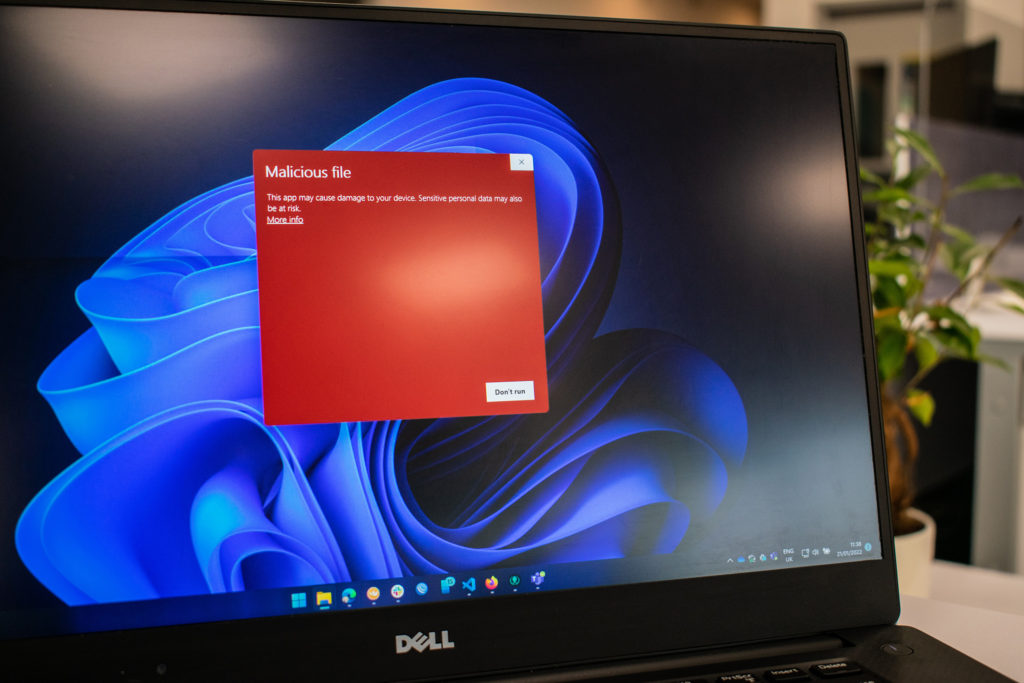
There are several types of malware, each with a somewhat different purpose, and many different reasons people write it I’ve compiled a few of them here, but there are always more.
Some people find it fun

There have always been people who like to break or vandalize things. Computers are no different. There is also a subset of people, usually younger and still learning who write things like viruses to learn how they work. They don’t necessarily intend for it to get into the wild, but sometimes it does.
They want to co-opt your computer

There are a lot of reasons someone might want to use “spare” computing power on your computer, but a lot of malware uses your computer to do some sort of task, from sending spam, to crypto-coin mining, to password cracking. They also generally write the malware to also try to spread the software to other computers yours interacts with.
Identity theft

They want to get information about you. Whatever they can find that they can use to steal your identity. They may install something to log all of your keystrokes, or just monitor what you send over the internet. There are several methods someone could use to get your personal information if your computer is compromised.
Corporate Espionage

Companies often spy on each other. Some will do whatever they can to get the corporate secrets of the other. This can be a huge problem for companies, and the targets are generally computers inside a large company, which should have decent protections but often won’t. The increase in work from home with people using their personal computers for company work has made the home user more of a target.
Even if there are no corporate secrets on your home computer, malware is often indiscriminate. It will be written to target more than it needs to in order to make sure that it doesn’t miss anything important. While most corporate spies won’t be particularly interested in what is on your computer, some may find a nice secondary revenue stream by selling personal identity information. Even if they don’t want your information, and none of your data is of interest, the malware can often impact performance, and can still spread itself to other machines.
Holding your data for ransom

Ransomware is a subset of malware. It encrypts your entire hard drive, then it only allows your computer to display a screen saying that your data has been encrypted and that you must pay a certain amount to get your data back. The encryption algorithms used are very strong encryption that even the government can’t usually crack, so you have no hope of doing so. To keep things anonymous they usually require payment in Bitcoin or some other form of cryptocurrency.
If you actually do get ransomware, your options are to wipe the hard drive, and lose all of that data, or pay the ransom. Even if you do pay the ransom, you are dealing with liars and criminals, so there is no guarantee that they will decrypt your data. Luckily most targets of such are larger organizations who actually have the money to pay. It’s much the same reason poor people aren’t often kidnapped for ransom. You want a target who can pay and make the effort worthwhile. That said, it is still a possibility, so staying careful and running decent anti-virus will reduce the chances.
Anti-virus software
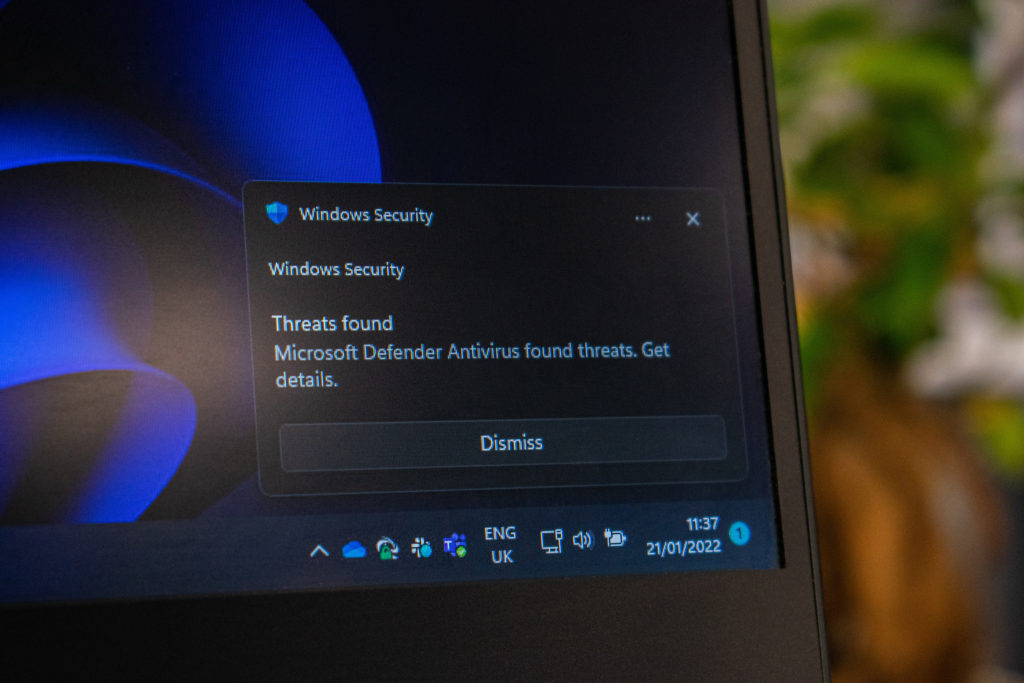
One of the first things you should do with a new machine to avoid malware online is set up a decent anti-virus package. Windows comes with Windows Security (formerly Windows Defender). It works pretty well and might be enough if you’re careful. Many security professionals consider Windows Security to be a little less capable, so I would also recommend adding a second package. While there are a lot of AV packages available for various costs, there are also several free AV packages. They do well enough to keep you reasonably clean. A paid AV product might give you a bit of added protection, but in my opinion, if you’re even moderately careful they aren’t really worth the cost unless you have the spare income and really want the extra peace of mind.
Online Hygiene

While it’s good to run a decent AV package, what has really kept me safe and helped me avoid malware online is being careful. To be honest, I consider the antivirus package to be plan B. I’ve been stupid a time or two and had to clean up the mess. More often, I’ve had to clean up someone else’s mess. Sometimes I couldn’t fix the problem without wiping the machine. I consider that a last resort.
So how do you keep yourself safe?
Keep your software up to date

If you wish to avoid malware online, then you must keep your software up-to-date. Most developers update their software regularly. It is important to keep the software you use to access anything online as up-to-date as possible. It is particularly important that you keep your operating system, your browser, and your anti-virus software as up-to-date as possible. You should also keep your router and modem software updated if you have the access to do so.
Have a firewall

A firewall is something that can monitor the data going between your computer and the outside world and analyze the individual packets. It can block the packets based on a set of defined security rules. It may block all of a certain kind of packet, or have any number of other rules.
There are two basic types of firewalls. Hardware firewalls go between your computer and the outside world. Software firewalls run on your computer. Both are useful. Windows includes a decent software firewall, though there are third-party firewalls that are more capable. Many routers and modems will act as an acceptable hardware firewall if you can learn to configure yours. You can also purchase external hardware firewalls that do a pretty good job. It’s even possible to build your own out of an old PC. Of course, how to do that is way beyond the scope of this article.
Browser script blockers

Ad blockers and script blockers for your browser can stop a lot of stuff. All browsers have vulnerabilities. The creators do a pretty good job of updating them to help keep you safe. However, many more people are working on ways around those protections. Blocking scripts and ads will help prevent some web pages from becoming vectors of infection. Some web pages won’t let you access them with a script blocker active. Others need certain scripts to function correctly. You generally have the option of whitelisting a particular page in the ad blocker, either temporarily or permanently, to let that page work as intended. Take note that even highly reputable ad servers have occasionally had malicious code disguised as an ad and compromised someone’s PC. With experience, you will learn what is and is not safe to put on the whitelist.
Learn to recognize deceptive popups
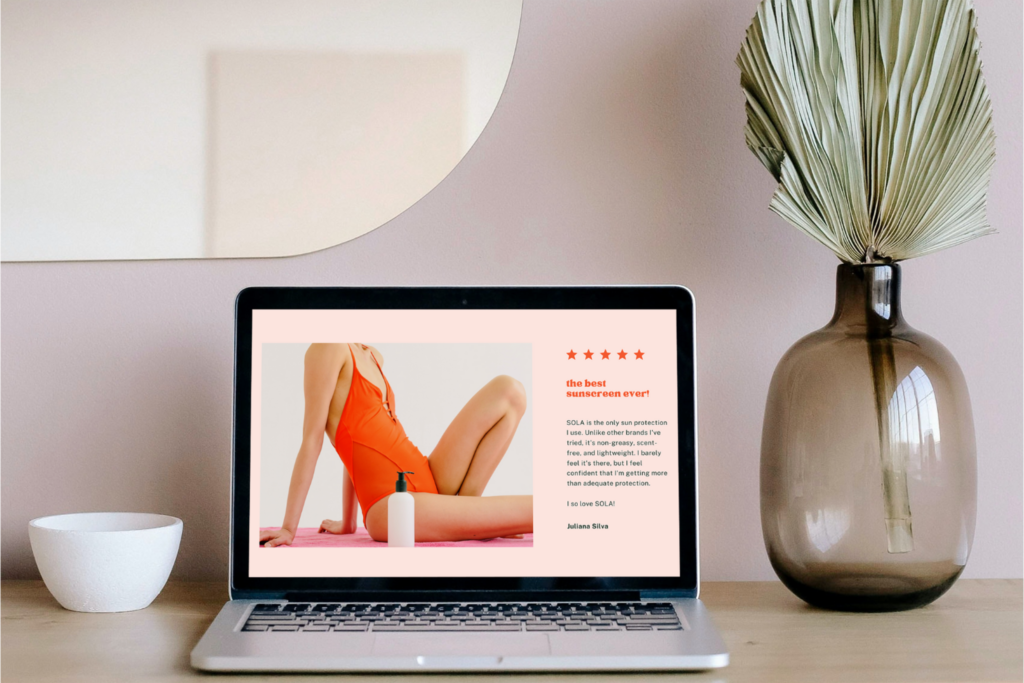
Sometimes you get a pop-up in your browser that is meant to look like a warning from your antivirus software. The idea is to trick you into clicking on it and installing their malware. Learn what your anti-virus software looks like, and learn what your browser pop-ups look like. If something pops up in the middle of the screen warning you about a virus or something, your first reaction should be to doubt it and check it out thoroughly. If you’re unsure, you could even leave it there and bring up your antivirus software without using the popup and run a scan.
Avoid “free” toolbars, screensavers, and similar

While there are a huge number of free software products that are legitimate, there are also a lot that are nothing short of a way to get something from you. The person who had tens of thousands of malware threats really liked a casual gaming app that offered her all sorts of little free games. I’d never heard of it, and I won’t mention its name here, but 30 seconds of research told me that it was basically a malware delivery tool. She also liked “free” screensavers. The screensavers did actually work and most looked pretty cool. However, each and every single one also came with a malware package attached to it.
Likewise, several malware packages will offer you some sort of “revolutionary” toolbar for your browser. Most of these don’t do anything useful and just compromise your system. If you want to add functionality to your browser, most browser providers have an online “store” where vetted extensions are available. Even these are not 100% but are generally safe. While there are legitimate browser extensions that cannot be placed in the online store for various reasons, unless you know what you’re doing, I recommend avoiding them.
Avoid software piracy

While I don’t want to get into the ethics or legalities of software piracy in this post, attempts to obtain illegitimate copies of paid software is one of the more common vectors of infection. Many websites that host, or purport to host cracked copies of software often host malware or malware-ridden copies instead. The bad guys use the cracked software as bait to entice you to compromise your PC. If you really, really know what you’re doing, you can find “safe” pirate sites. However, if you don’t, you WILL get something bad. Again the legal and ethical concerns of software piracy are a topic for a different post.
Be very careful with torrents

On the topic of piracy, using torrents for software, music, and video piracy is another extremely common vector for malware. If you don’t know what torrents are, then this isn’t really something that concerns you and you can probably skip this section, but I’ll do a quick explanation anyway.
To put it very simply, torrents are a way to send very large files by distributing them in small chunks among a large number of computers. That way nobody has to host the whole file. The .torrent file you click on isn’t actually the data you want, but kind of a directory to where the individual bits of the data in question is being hosted. Your browser usually can’t handle torrents and you need special software to download them.
There are a lot of completely legal, ethical, and legitimate reasons to use torrents. They are also commonly used for piracy and, like the piracy above, they are commonly used as a means to compromise other PCs. Again as above, if you know what you’re doing you may be able to do it safely, but if you don’t, you WILL get malware.
Avoid pornographic material

I also don’t want to discuss the ethics of pornographic websites. There are some that are “legitimate”, in that they are very careful about not hosting or transmitting malware. There are also a huge number that are not. Like the various forms of piracy, the material and websites are often used as bait to get you do something to compromise your PC. Again, if you know what you’re doing, you can generally do it safely, but if not, your PC WILL get compromised.
Avoid Clicking on ads

Ads might keep the websites you use running, but some are deceptive. Malicious ads have gotten through even legitimate ad servers. More often than not you are better off ignoring the ads, even if you don’t block them. Now, if you know the company, you can generally get away with clicking on the ad. Even still be careful. Bad actors have created things that look like legitimate ads but are not. If an ad is telling you that your computer is infected or at risk, you can generally assume that the people who put it out don’t have your best interests at heart.
Be very careful of email attachments.

While email attachments are a bit of an older vector for malware, it still happens rather frequently. In fact, email attachments are usually the first way people learn to avoid malware online. Email viruses often have some sort of software or attachment that then does something bad. Some malware can even find your address book and email itself to everyone you know. If you weren’t expecting the attachment, be very wary of it. There is good news though. A lot of email providers do things to scan email for malicious attachments, so you might not even get them. However, it does depend on your specific email provider. Even then some things sometimes get through.
Learn to read the URL

A URL stands for “uniform resource locator”. It is the web address of whatever you are looking at. It shows up at the top of your browser. Every web page, and even pictures on that web page, has a URL. URLs can be faked, or otherwise made deceptive in a number of ways. If you hold your mouse over a link, you will see the URL of wherever that link leads show up, usually at the bottom of the browser window. Get in the habit of at least glancing at that to see if it seems to be taking you where it should.
How to read a URL is another post, but with practice, most people should be able to figure it out with some effort. One situation to be aware of is the existence of URL shorteners. If you have a very long URL, you can use a service to create a much shorter URL. The service then redirects to the URL you want. URL shorteners can be handy in a lot of situations, but they can also be used to trick you into clicking on malicious links. Be very careful if you click on one.
Conclusion
There are a lot more things you can do to keep yourself safe. I’ve hit a few here, but there are always more. If you are careful, you can generally avoid malware online. Running a good anti-virus package is important, but the best malware protection you can have is the one that goes in between your keyboard and chair.
If, for some reason, you failed to avoid malware online and infected your computer, then give me a call. I’ll happily help you clean all that malicious code off of your computer.